How does an authenticator work?
Previously, I talked about what 2FA is and how it works. Today, I will be covering another approach for 2FA — Authenticator. If you are already using an authenticator for 2FA, you will know there are different choices of authenticators in the market. They are using the same standard for generating authentication codes. Are you ready for this topic? Let’s get started.
Types of Authenticator Algorithms
Basically, authenticator algorithms can be grouped into 2 types:
Time-based One-time Password (TOTP)
Simply put, this algorithm is based on the current timestamp with a secret key to generate a passcode. TOTP is also known as software token and app-based authentication.
HMAC-based One-time Password (HOTP)
HOTP is similar to TOTP. But instead of using the current timestamp, HOTP is based on a counter with a secret key to compute a passcode. For example, Yubikey is using the HOTP algorithm. (In case you don’t know, Yubikey is a hardware token that is used to verify user identity)
In this post, I am going to share the TOTP algorithm.
How Does an Authenticator Work?
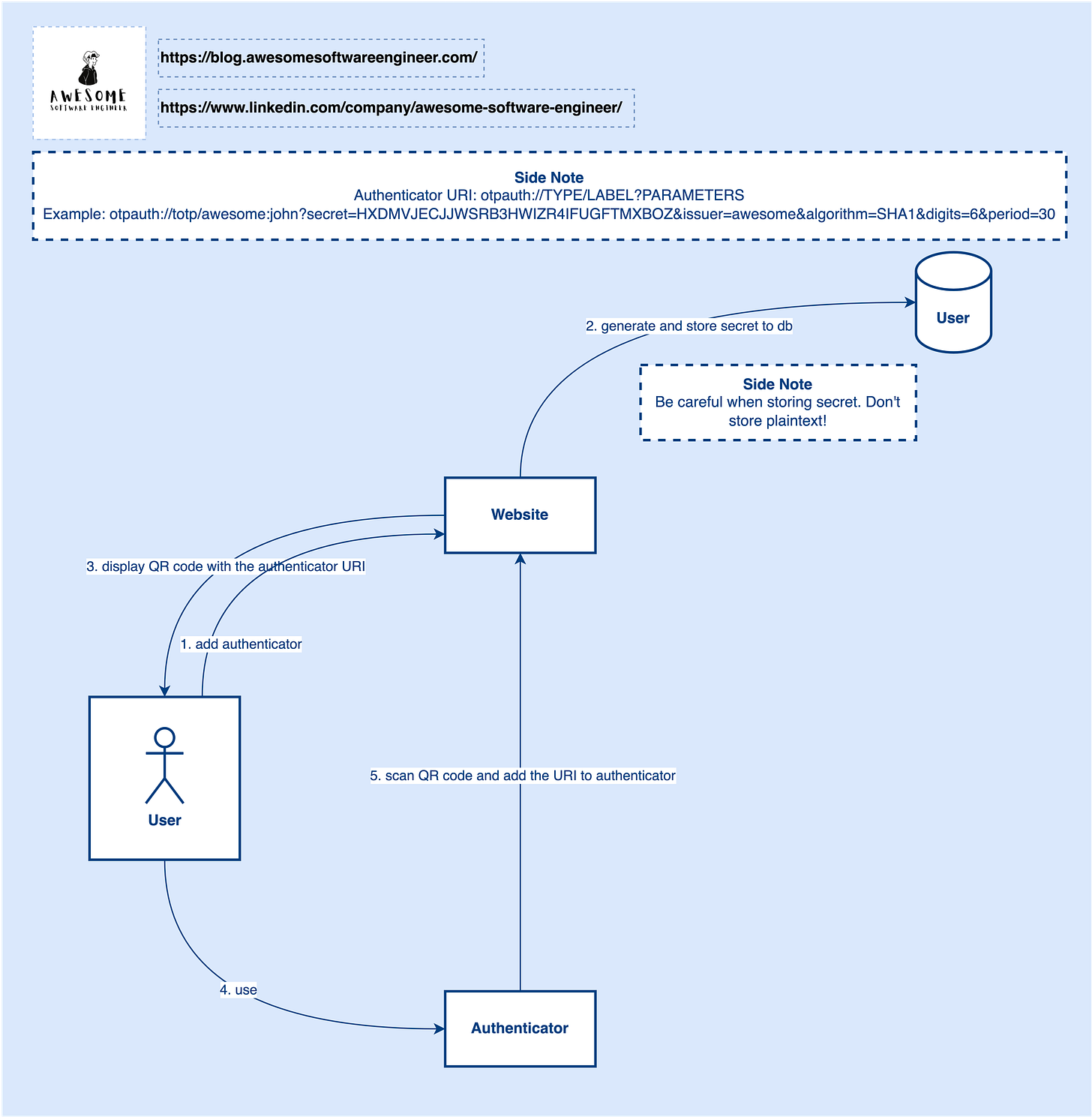
To make this 2FA approach work, there are 2 steps:
Step 1, the user needs to enable the authenticator.
In this step, the authenticator URI will be included in the QR code and displayed in the frontend for users to scan. Once scanned, a record will be created on the authenticator and the OTP will be refreshed in every 30s or other intervals.
For the details of the authenticator URI, you can refer to Google Authenticator (https://github.com/google/google-authenticator/wiki/Key-Uri-Format)
Step 2, the user needs to input the OTP generated by the authenticator in every login.
In this step, the website will use the same secret and current timestamp to generate a code and compare the code with the OTP from the user to see if it is valid.
TOTP Algorithm
TOTP is based on symmetric key cryptography. A secret key is shared between two parties (client and server). Both parties use the same key to generate and verify the OTP.
In case you don’t know what is symmetric key cryptography, go check out this post about encryption:
Clock Skew Problem
TOTP is based on a timestamp and there is a time synchronization problem between the client and server. It can cause the generated code to be different in the client and server. To solve this problem, the TOTP algorithm will use multiple time slots to verify the code instead of only the current time slot. So, even if the code gets updated on the authenticator, you can still use it for authentication (only if within the valid time slots).
Replay Attack
When a user inputs a valid OTP to the system, it is possible to have a replay attack vulnerability if you don’t mark the OTP as used after. To avoid this issue, we can store the OTP in a cache for a short period till the OTP expires. When the same user login, we first look up whether the OTP gets used or not. If the OTP gets used, then reject the request, else allow it.
Storing Secret Key
To protect the secret key, we should use a strong encryption algorithm (e.g. RSA) to encrypt the secret key before storing it in the database. Don’t store the secret key in plaintext!
Your Turn
Do you think it is possible to conduct a brute-force attack on the OTP given that the code changed every 30s? If yes, how to avoid it? If not, why?